Remote packet capturing¶
Routing Active Testing supports two ways of capturing traffic for packet-by-packet analysis using a packet analyzer such as Wireshark.
Non-live packet capture: This method captures traffic on Test Agent interfaces; the traffic can subsequently be downloaded to your PC. The method is accessed from Apps in the main menu.
Advantages: Can be used to capture traffic behind NAT. Distributed captures can be easily triggered.
Disadvantages: No real-time capturing. Size of capture is limited.
Live packet capture: This method captures traffic in real time by forwarding all traffic from the Test Agent directly to Wireshark. The method is accessed under Test Agents by clicking on a Test Agent, then clicking the Applications tab.
Advantages: You can capture much more traffic, since the traffic is not stored on the Test Agents, and you can track the capture in real time.
Disadvantages: Capture behind NAT is not supported (you need a direct connection to the IP address). Distributed captures are not as easy.
Read more about these capture methods below.
Non-live packet capture¶
Use this method to capture real user traffic on any of your Test Agent interfaces directly from your Routing Active Testing account.
You can start a capture on multiple interfaces in parallel, and you will see the number of captured packets updated live. When the specified number of packets have been captured, you can download the capture as a .pcap file. If the capture takes too long, you can cancel the capture at any time and still download the packets captured up until that point.
To configure this method, specify the parameters below, then start the capture by clicking the Start button.
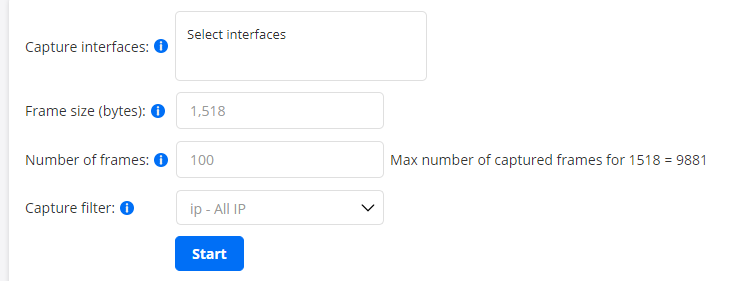
Capture interfaces: Select the Test Agent interfaces on which to perform the packet capture.
Frame size (bytes): The maximum number of bytes to be captured of each packet.
Default: 65,535.Number of frames: The maximum number of packets to be captured on each interface. The maximum depends on the size of each packet, since the total allocated memory is 15 MB.
Capture filter: Only packets matching this filter will be captured. The tcpdump/Wireshark filter format is used.
The maximum size of the capture buffer is 15 MB. This means 245,760 packets with Packet size = 64 bytes, or 10,361 packets with Packet size = 1518 bytes. The higher you set Packet size, the fewer packets you will get. Also please note that the download of captured data may time out if the Test Agent management connection is too slow.
The packet capture filter follows the same format as the capture filters in Wireshark. For the syntax of these filters, refer to the Wireshark capture filters wiki.
Some useful predefined filters are available:
Filter |
Function |
|---|---|
ip |
All IP |
udp |
All UDP |
tcp |
All TCP |
icmp |
All ICMP |
udp port 53 |
DNS |
tcp port 80 |
HTTP |
port 5060 or port 5061 |
SIP |
tcp port 143 |
IMAP only |
udp port 161 |
SNMP only |
You can also create your own capture filters.
After the capture has finished, you have the option to download and open a .pcap file in Wireshark or in some other packet analyzer of your choice.
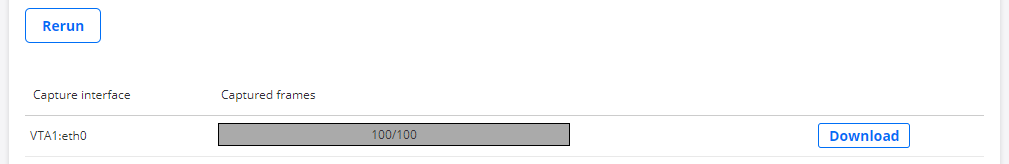
For security reasons, the captured data is not stored on the Test Agents, nor on the Routing Active Testing server, and is available only as long as you stay on the Remote Packet Capture page.
Live packet capture¶
To enable the live capture in the menu, click the Test Agent in the Test Agents view, then select the Applications tab.
Select a capture interface in the Capture interface column.
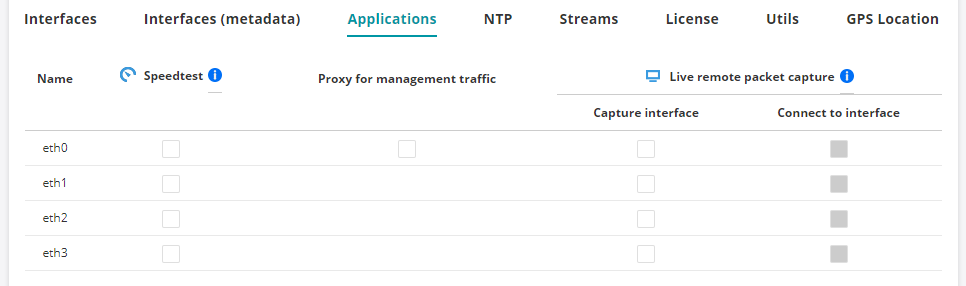
A dialog appears where you also get to select which interface to connect to (the two can be different):
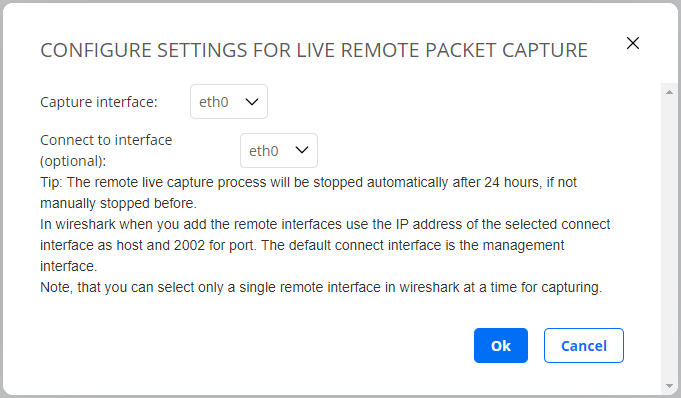
In Wireshark, when adding the remote interfaces, use the IP address of the selected connect interface as host, and use 2002 for port. The default connect interface is the management interface.
For more information on how to capture traffic from remote interfaces using Wireshark, go here and search for “remote interfaces”.
Note
Live packet capture requires the WinPcap library. It does not work with the Npcap library introduced as the default for packet capture in Wireshark 3.0.