Fragmented DHCP packets¶
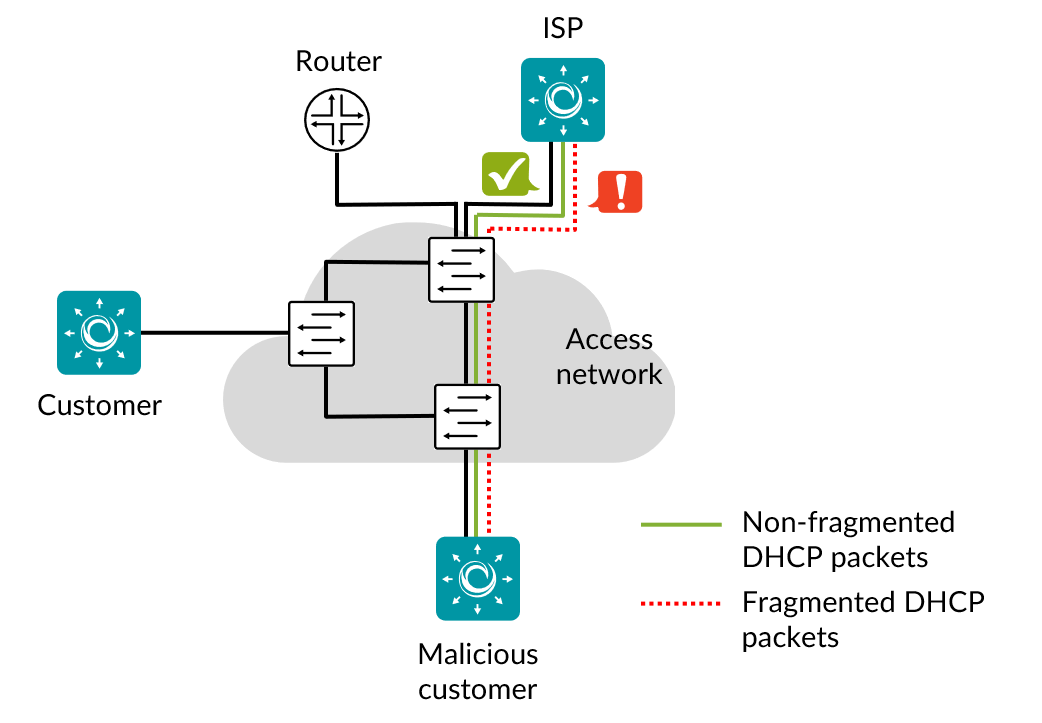
This task checks that the switch drops fragmented DHCP packets before they reach the control plane. If fragmented packets are not dropped, they will consume resources at the switch’s control plane upon reassembly. This fact can be exploited to launch a DoS attack causing the CPU to run out of cycles or filling up the packet buffers.
Since the control plane is normally in a controlled environment, the MTU is known. There is therefore no reason for packets to be fragmented, nor for packet reassembly to be needed.
References¶
The test performed conforms to SAVI section 3.1.2.
Impact¶
DoS
Test procedure¶
Customer sends a valid DHCP packet.
Customer sends DHCP packets fragmented into 40 byte and 104 byte fragments.
Fail criteria¶
ISP does not receive the valid DHCP packet.
ISP receives any fragment of a fragmented packet.
Parameters¶
General¶
Customer: A Test Agent interface acting as a customer.
ISP: A Test Agent interface acting as a central node on a trusted port. The test requires that the ISP reside in the same Layer 2 network as the customers.