Introduction to security testing¶
The security tests in Routing Active Testing are primarily designed for Layer 3 networks. However, all issues should be tested independently of what type of network design or topology is used. Our experience shows that the potential for configuration errors exists in any network and can give rise to security issues. Most of the security issues tested in Routing Active Testing cannot be mitigated by end-users; it is the network that must provide protection.
The Routing Active Testing security tests focus mainly on:
Man-in-the-middle (MITM) attacks: The ability to eavesdrop and possibly change traffic without the customer being aware of it.
Denial-of-service (DoS) attacks: The ability for one customer to affect the services of one or several other customers.
Abuse – Tracking of end-users (IP addresses): The ability to identify a customer if there has been some incorrect usage of the services.
Routing Active Testing supports security testing on the IPv4 protocol.
To perform security tests, one or two Test Agents are needed. Two interfaces must be used on each Test Agent: one agent interface is used for testing, and the other (“eth0”) is used to maintain the encrypted management connection to the Routing Active Testing cloud servers.
Test Agents play one of the following roles in security tests:
Customer: A customer attempting a particular operation. Each Test Agent interface playing this role is connected as a standard customer to an access port.
ISP: Internet Service Provider, placed in a trusted zone. Only one Test Agent interface plays this role.
The picture below shows an example of a test configuration.
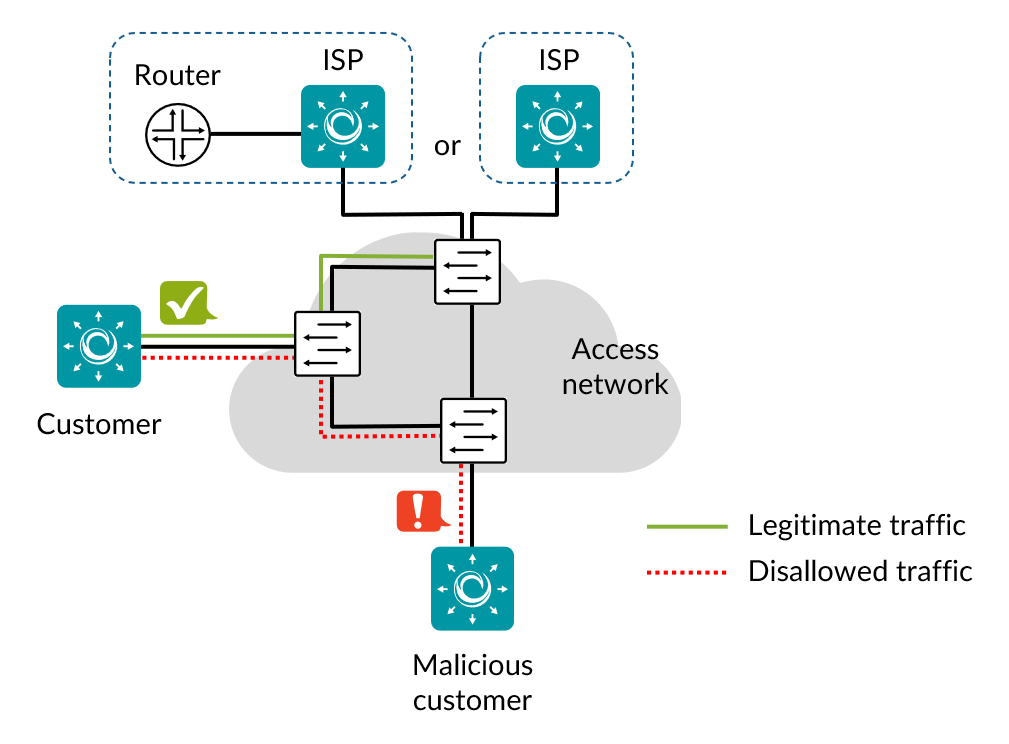
It is most convenient to place the ISP Test Agent in the same Layer 2 network as customers, as this is required for some of the tests (though not for all of them; the requirement is noted for each task type to which it applies). This setup makes it possible to run all security tests using the same network configuration.
It is also possible to place the ISP Test Agent in the Layer 3 network, as depicted below.
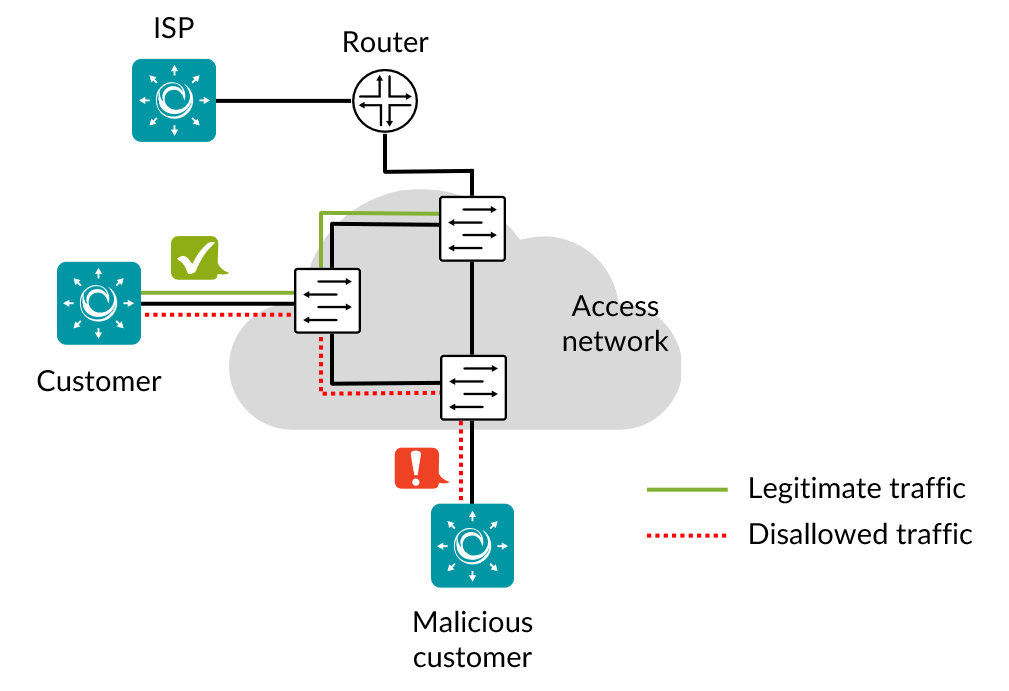
The description of each task type has a reference to the corresponding identification in SAVI.
A few of the tests require a DHCP server and a multicast sender, neither of which is normally provided by the ISP Test Agent.
The DHCP server requirement can be met by setting up the ISP Test Agent as a DHCP server, or by using an external DHCP server connected to the network.
A multicast sender can either distribute real multicast traffic, or it can consist of a lab setup. A multicast source must be available in the network for tests involving multicast/IGMP.
See this page for an overview of all supported security features.