Fragmented TCP/UDP headers¶
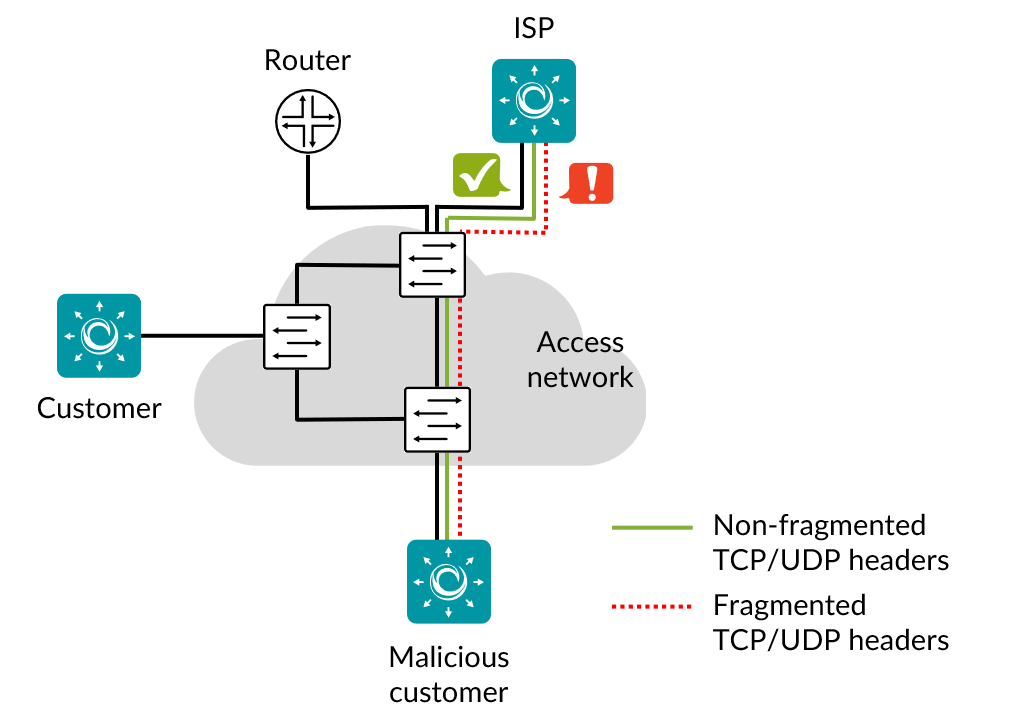
This task checks that the switch drops IPv4 and IPv6 packets with fragmented headers. By fragmenting TCP or UDP headers it is possible to bypass access lists which are based on information in those headers. The test verifies that packets with a small fragment offset are blocked/dropped.
References¶
The test performed conforms to SAVI section 3.1.2.
Impact¶
DoS, Abuse, Illegal access to content
Test procedure¶
Customer sends non-fragmented TCP and UDP packets to ISP.
Customer sends similar packets fragmented into 8 and 16 byte fragments.
Fail criteria¶
ISP does not receive the non-fragmented packets.
ISP receives all fragments of a fragmented packet.
Parameters¶
General¶
Customer: A Test Agent interface acting as a customer.
ISP: A Test Agent interface acting as a central node on a trusted port.
Advanced¶
Source UDP/TCP port: Source UDP or TCP port for traffic sent from Customer to ISP. Range: 1 … 65535. Default: 41234.
Destination UDP/TCP port: Destination UDP/TCP port for traffic sent from Customer to ISP. Range: 1 … 65535. Default: 24567.