Router redundancy protocol listening¶
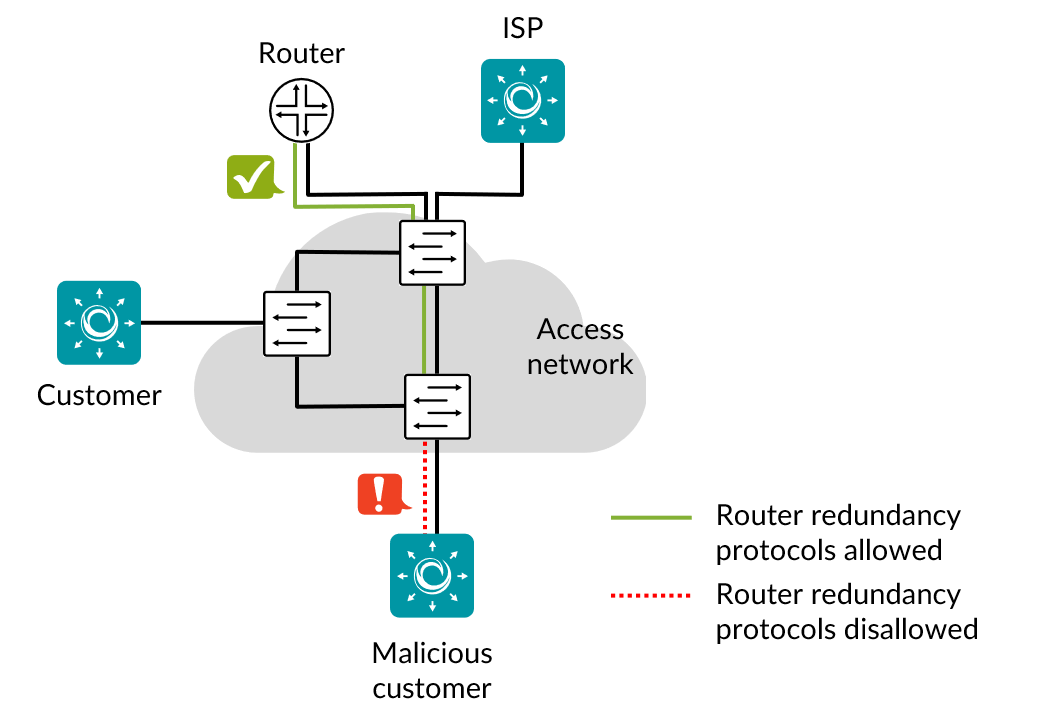
This task checks that router redundancy protocols are unavailable at customer ports. If such protocols are available, a malicious customer can sniff the protocols and then force other customers to point their default traffic route to the malicious customer, thus launching a man-in-the-middle (MITM) attack.
Note
For this task, routers must be present in the network. The test cannot be performed against switches only.
Tested protocols:
VRRP/CARP
GLBP
HSRP
References¶
The test performed conforms to SAVI section 3.1.7.
Impact¶
MITM, DoS
Test procedure¶
Customer listens during 60 seconds for traffic on each of the above protocols.
Fail criteria¶
A packet from any router redundancy protocol is received by Customer.
Parameters¶
General¶
Customer: A Test Agent interface acting as a customer.
ISP: A Test Agent interface acting as a central node on a trusted port.